I know, it sounds like some sort of sci-fi tale, but it is possible for someone to extract meaningful data from the electrical power line feeding your computer without even touching it. For the reader who is only hearing about this type of threat for the first time, I hope this article meets you before you become a victim. For those of you who have been a victim, or are taking steps to prevent being a victim, you will find relief in knowing that Bantam Technology has you protected.
Please read on.
What is a Power Line Exploitation? A PLE occurs when signals present on the electrical supply line are found to contain meaningful information after being acquired and analyzed via direct contact or via “air-gapped” methods
What is generating these signals in my computer? Power supplies that convert AC to DC create voltage and current harmonics. It is even possible to detect a pattern of harmonics from a power supply that is unique to a manufacturer, thus providing a way to identify a device based on the brand of power supply. The signals migrate outward from the server on the electrical supply wires, past the equipment rack power distribution unit (PDU) and ultimately outside of the facility. The matter is complicated by the fact that these signals are also communicated onto the grounding path which must maintain its integrity to protecting human life.
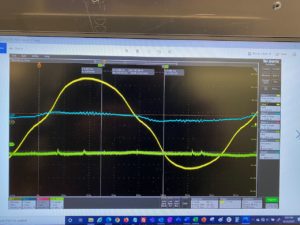
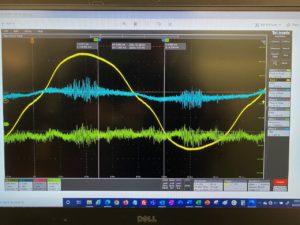 This is an image from an oscilloscope showing electrical signals captured from the power cord of a modern server that can be used for a Power Line Exploitation. Keeping it simple, the yellow wave form is the expected 60Hz voltage signal used for reference. The blue line is the current waveform with the 60Hz waveform and superimposed current harmonics and data signals present at various frequencies. The green line is measured current on the grounding path. There should be nothing on this green line. Instead, the signals found on the blue line are “communicated” or coupled onto the ground path, where they move away from the computer to the outside world for capture by a threat actor.
This is an image from an oscilloscope showing electrical signals captured from the power cord of a modern server that can be used for a Power Line Exploitation. Keeping it simple, the yellow wave form is the expected 60Hz voltage signal used for reference. The blue line is the current waveform with the 60Hz waveform and superimposed current harmonics and data signals present at various frequencies. The green line is measured current on the grounding path. There should be nothing on this green line. Instead, the signals found on the blue line are “communicated” or coupled onto the ground path, where they move away from the computer to the outside world for capture by a threat actor.
Is this real? One only needs to read this recent IEEE paper to see how to perform a PLE. Now that this information is out there, expect lots of people to try it out.
How do I know if I have been the victim of a PLE? A data breach has occurred via no detectable means. The server contains current operating system patches and anti-virus/anti-malware software. Network access to the server is controlled and restricted via IP or MAC blacklists and whitelists. Logins are monitored and password strength and rotation policies are enforced. The server itself is in a cage with restricted personnel access. No explanation for how the breach has occurred exists.
How do I prevent a PLE? Every Bantam Technology product ever offered has been able to mitigate a PLE – that is no accident. We have known about this type of threat long before it got the acronym PLE. In response to the growing importance of remediating against a PLE, however, we are happy to offer to manufacturers, for the first time, a component that you can use to build up your own custom solution, such as a UPS, PDU, or standalone enclosure. Please check out the SA3600 Commercial Spec Sheet – 2020 for details and contact us for ordering information. The Bantam SA3600A is designed specifically to permanently remove any identifiable electrical signals – and the patterns they represent – on all of the electrical paths.
We have kept our promise for over 15 years that Bantam Technology is the best solution for your high-value electronics, and we mean it. The PLE threat is real and Bantam Technology is here with real protection against it.